
Cyberattacks are increasing in frequency and intensity, targeting businesses of all sizes across industries. The need to have robust cybersecurity measures in place to protect your business has never been greater.
There is no one-size-fits-all approach to cybersecurity, so how do you determine which cybersecurity framework is best suited to the needs and vulnerabilities of your organization? We go on to discuss the main types of cybersecurity frameworks and how you can select the right one for your business.
What is a Cybersecurity Framework?
A cybersecurity framework is a comprehensive set of policies, procedures, standards and guidelines that a business implements and maintains to minimize the risk and impact of hacking attempts, data breaches and other cyberattacks.
The focus and content of cybersecurity frameworks vary substantially. Some, such as the General Data Protection Regulation (GDPR), are generic while others are designed for application in specific industries or purposes, such as the Health Insurance Portability and Accountability Act (HIPAA). Cybersecurity frameworks can also either be voluntarily adopted by organizations, or mandatory for meeting certain industry compliance requirements, as with the HIPAA and the GDPR.
What all cybersecurity frameworks share in common, however, is that they help organizations identify potential cybersecurity threats, reduce their vulnerabilities, and mitigate the damage caused by a security incident.
The Importance of Implementing a Cybersecurity Framework
Implementing a cybersecurity framework offers multiple benefits to businesses, whether or not it is mandatory. These include:
Enhanced Security
Cybersecurity frameworks provide a systematic approach to identifying and managing cybersecurity threats, which helps businesses improve their overall information security.
This greatly reduces the likelihood of data breaches and loss, illegitimate access to sensitive information, and virus or malware attacks.
Compliance and Reputation
Some cybersecurity frameworks are mandatory for organizations operating in certain industries, such as healthcare and finance. In these cases, businesses need to comply with the relevant cybersecurity laws and regulations to avoid sanctions and penalties.
However, even for voluntary cybersecurity frameworks, compliance is nonetheless important for the reputation of your business. By adopting accepted industry standards, you demonstrate to potential clients and customers that your business can be trusted to take the protection of data seriously.
Improved Efficiency
Without a cybersecurity framework in place, organizations will react to cyberattacks, rather than anticipate them in advance.
This ultimately incurs much greater costs than implementing a cybersecurity framework that streamlines security processes and improves the efficiency of identifying, preventing, and responding to security incidents.
Types of Cybersecurity Frameworks
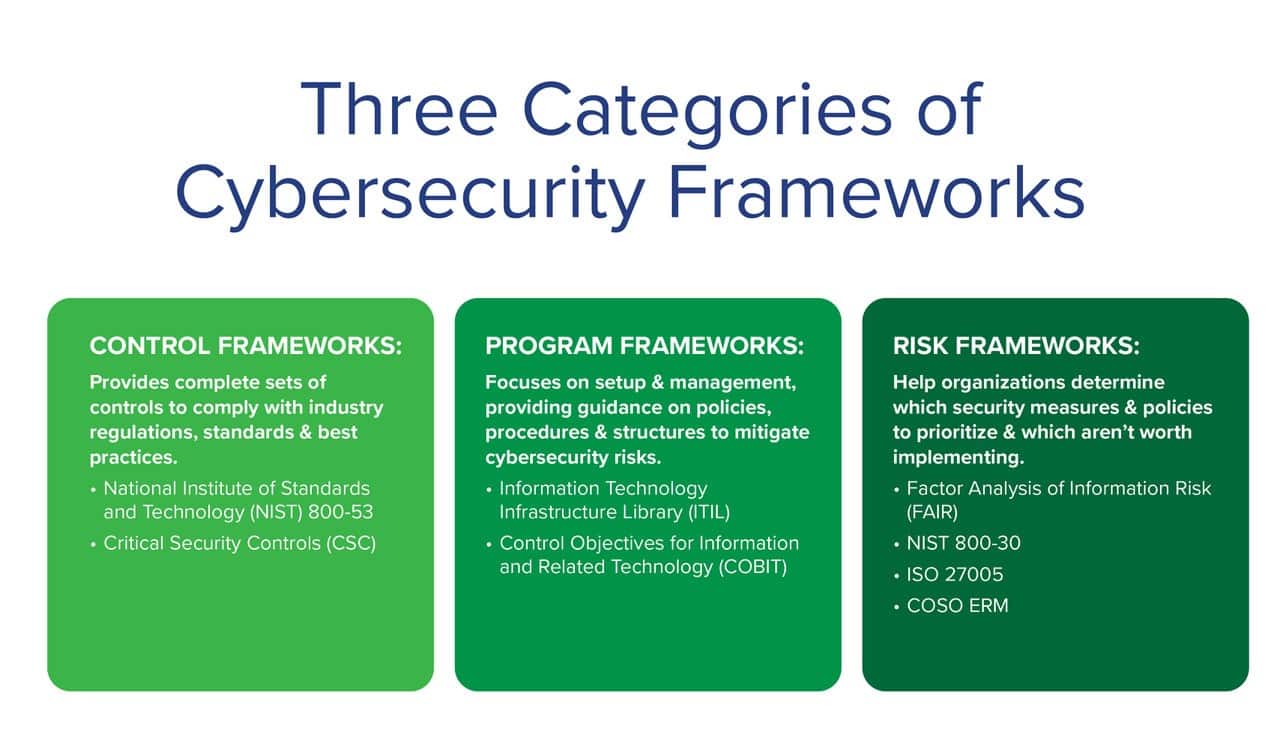
To better understand the different ways that a cybersecurity framework can function, it is useful to divide them into three broad categories. These are:
Control Frameworks
Control frameworks provide complete sets of controls that businesses can implement to comply with industry regulations, standards and best practices. These frameworks typically include an extensive list of security controls, procedures and guidelines, covering all areas of cybersecurity.
Some of the most widely-used control frameworks include the National Institute of Standards and Technology (NIST) 800-53 and the Critical Security Controls (CSC) developed by the Center for Internet Security (CIS).
NIST 800-53 outlines an array of potential security controls applicable to any organization but groups them into low, moderate and high-impact levels so you can determine which is appropriate for your business.
The CSC, meanwhile, details twenty useful security controls that have been proven to mitigate the impact of the most common cybersecurity threats.
Program Frameworks
While control frameworks concern many of the technical aspects of cybersecurity, program frameworks focus on their setup and management, providing guidance on developing policies, procedures and structures to mitigate cybersecurity risks.
A program framework, in a sense, acts as a style guide that provides overall direction and structure to your organization’s cybersecurity strategy.
This may include, for instance, the creation of metrics to check for expected outcomes, the establishment of communication channels between IT employees and management, and the performance of an internal or external cybersecurity audit.
Some of the most popular program frameworks include the Information Technology Infrastructure Library (ITIL) and the Control Objectives for Information and Related Technology (COBIT).
ITIL provides a comprehensive set of best practices in IT Service Management (ITSM), focusing on aligning IT services with the business’s goals and objectives. It aims to improve the quality of IT services by prioritizing and addressing the most pressing needs of the organization.
Risk Frameworks
Risk frameworks help organizations to determine which security measures and policies to prioritize, and which perhaps aren’t worth implementing, depending on the needs and goals of the business.
There are many risk frameworks for cybersecurity, including NIST 800-30, ISO 27005, and COSO ERM. In general, these risk frameworks take a qualitative approach to risk analysis but this can be complemented by the Factor Analysis of Information Risk (FAIR) framework which uses a quantitative method.
Most Commonly Used Cybersecurity Frameworks
NIST Cybersecurity Framework
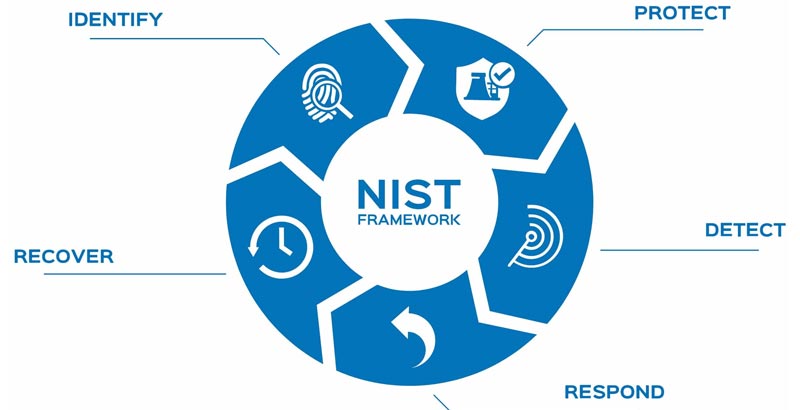
The NIST Cybersecurity Framework is widely viewed as the gold standard of cybersecurity. It has been adopted across businesses of all sizes and industries, owing to its flexible and scalable approach to cybersecurity.
It focuses on five core functions – identify, protect, detect, respond, and recover – that are easy to understand, helping to demystify complex cybersecurity practices and terminology so it can be understood easily by an organization’s employees.
ISO 27001

ISO 27001 is an internationally recognized standard for information security management systems (ISMS), designed to provide a comprehensive approach to managing sensitive information.
It guides organizations of all sizes and from all sectors on how to establish, implement, maintain, and continually improve an ISMS to reduce the occurrence of data breaches and losses of sensitive information.
CIS Controls

CIS Controls are used by thousands of organizations as a baseline for determining the effectiveness of their cybersecurity protocols.
It comprises a set of twenty recommended actions for deterring the most common cyberattacks, including steps to protect inventory, control hardware assets, and recover lost data.
As such, it does not have the breadth of NIST or ISO 27001 but its prioritized set of actions is extremely effective at ensuring businesses are not vulnerable to the most pervasive forms of cyber attacks.
Payment Card Industry Data Security Standard (PCI DSS)

PCI DSS is a widely used compliance framework that requires organizations processing credit card payments to implement strict controls that work to ensure sensitive information is protected.
The framework covers a broad range of security controls, including network security, access controls, vulnerability management and data encryption.
Organizations that handle credit card transactions must comply with the PCI DSS standards to avoid substantial fines and penalties in the event of a breach.
How to Choose the Right Cybersecurity Framework for Your Business
It’s often the case that the best cybersecurity framework for a business is predetermined due to it being either legally mandated or highly recommended in order to remain competitive.
However, it is invariably a good idea to go beyond the minimum of what is required when it comes to cybersecurity. But which cybersecurity framework to adopt? And to what extent? To help you answer these questions, it’s useful to keep the following factors in mind:
1. Industry Requirements
This one appears obvious but it bears repeating that businesses must consider their industry-specific regulations, such as GDPR or HIPAA, and select a framework that aligns with the relevant compliance requirements.
2. Framework Scope
Businesses must also consider the scope of the framework they opt for. Some frameworks cover everything to do with cybersecurity, while others focus on specific areas, such as risk management or compliance.
Your organization needs to choose a framework that covers all areas of cybersecurity relevant to its operations and, ideally, one that goes deeper into the most important aspects of the business.
3. Customization
The cybersecurity framework should be customizable to cater to the unique needs of the business.
NIST, for example, is an extremely comprehensive cybersecurity framework. Much of it might not be relevant or pressing for your business but it offers the possibility of adapting its guidance to your specific security needs and risk factors.
4. Budget and Resources
The cost of implementing a cybersecurity framework must be factored into the decision-making process.
While it would be nice to be able to adopt and implement an all-encompassing cybersecurity framework that takes into account all eventualities, this might not be realistic. Instead, you need to choose a framework that fits within the budget and resources available while providing maximum protection against cybersecurity risks.
5. Ease of Implementation and Maintenance
In a similar manner to the constraints imposed by the available budget and resources, your business should choose a framework that is easy to understand for all employees and realistic to implement and maintain long-term.
A cybersecurity framework, after all, is only as effective as its implementation in practice. If the complexity involved exceeds the capacity of your business, it is likely to be more of a drain than a benefit.
Selecting and Implementing Cybersecurity Frameworks with Vertikal6
Knowing where to start when it comes to choosing and implementing cybersecurity frameworks is daunting for many small to mid-size organizations.
The potential cybersecurity threats often seem to exceed the capacity of many businesses to prepare and respond effectively to them.
At Vertikal6, we can guide you through this process and partner with you to put the right cybersecurity frameworks into effect for your business. Our team has expert knowledge of all the major cybersecurity frameworks and regulatory requirements that ensures your organization is as sufficiently protected and compliant.
From an initial assessment of your cybersecurity posture to the implementation and maintenance of appropriate cybersecurity policies and controls, we can help your business meet and exceed industry cybersecurity standards.
Get in touch with one of our expert advisors and get started on choosing the right cybersecurity framework for your business.
Start here to level up your IT.
Click below or call our Rhode Island headquarters at: 401-825-4400.









